How to Protect Company Internal Data and Website Management Backend to Prevent Data Breaches?
In today's fast-paced digital and information age, securing internal company data, such as internal videos, source code, management backends, engineering drawings, and financial documents, is an essential concern for every business. Unauthorized access or data breaches can lead to the loss of intellectual property, financial damage, or harm to the company's reputation. Therefore, developing a comprehensive encryption strategy is crucial. Below, we outline how to effectively encrypt corporate data and secure the website backend with advanced technical solutions.
1. Encryption of Company Internal Data
-
Convert Various Document Formats into Secure Formats
Internal company documents, often in Word, Excel, or PowerPoint formats, are easily copied and distributed if not encrypted.
- • For critical documents, reports, images, or blueprints, use specialized tools to convert them into PDF format, followed by encryption. This includes setting passwords and restricting editing or printing permissions, ensuring access is limited to authorized personnel.
- • For multimedia files like internal videos or audio, deploy DRM (Digital Rights Management) solutions for protection.
- For some multimedia materials, such as internal videos and audios of the company, the DRM (Digital Rights Management) solution can be directly used to protect them. For more details, please refer to previous articles. "A Comparative Study of DRM-X, Widevine DRM, and VdoCipher Digital Rights Management (DRM) Technologies".
-
Access Control and Permission Management
- Implement strict file access permissions through encryption, such as limiting printing, disabling copying, and setting file expiration dates or access counts.
- Bind files to user hardware to prevent unauthorized sharing.
- Employ graded management of employees, authorizing varying levels of access and generating usage reports.
-
SmallPDF Online Encryption
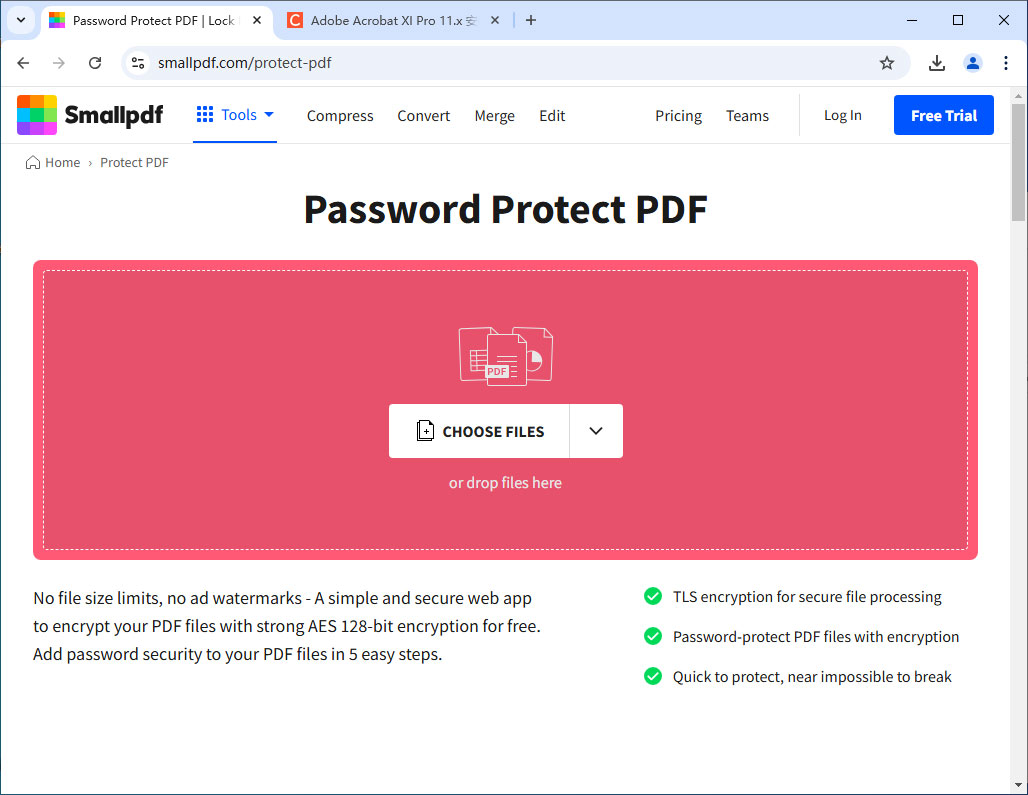
- Features: Supports online encryption with simple operation, suitable for non-technical users. Allows setting passwords to protect files and restrict editing permissions.
- Advantages: Simple to use, requires no software download, and offers password protection.
- Disadvantages: Cannot prevent screenshots or screen recordings.
-
Adobe Acrobat PDF Encryption
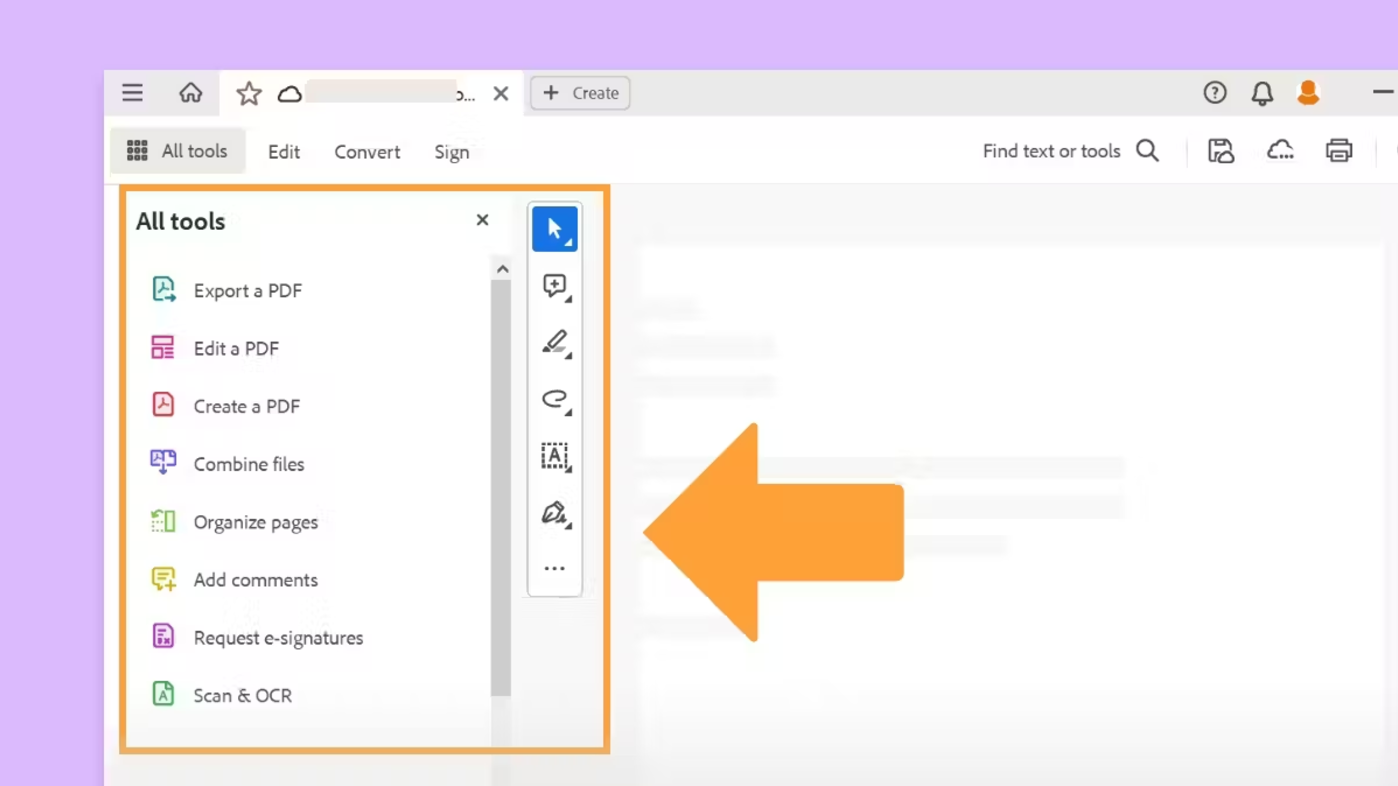
- Features: Provides robust encryption features to restrict document editing and printing. Encrypted PDF files require Adobe Acrobat or compatible PDF software for opening. Allows setting passwords for opening documents to enhance file security.
- Advantages: Comprehensive encryption options and industry-standard compatibility.
- Disadvantages: Vulnerable to screenshot-based breaches; shared passwords pose risks.
-
DRM-X 4.0 PDF Encryption Software
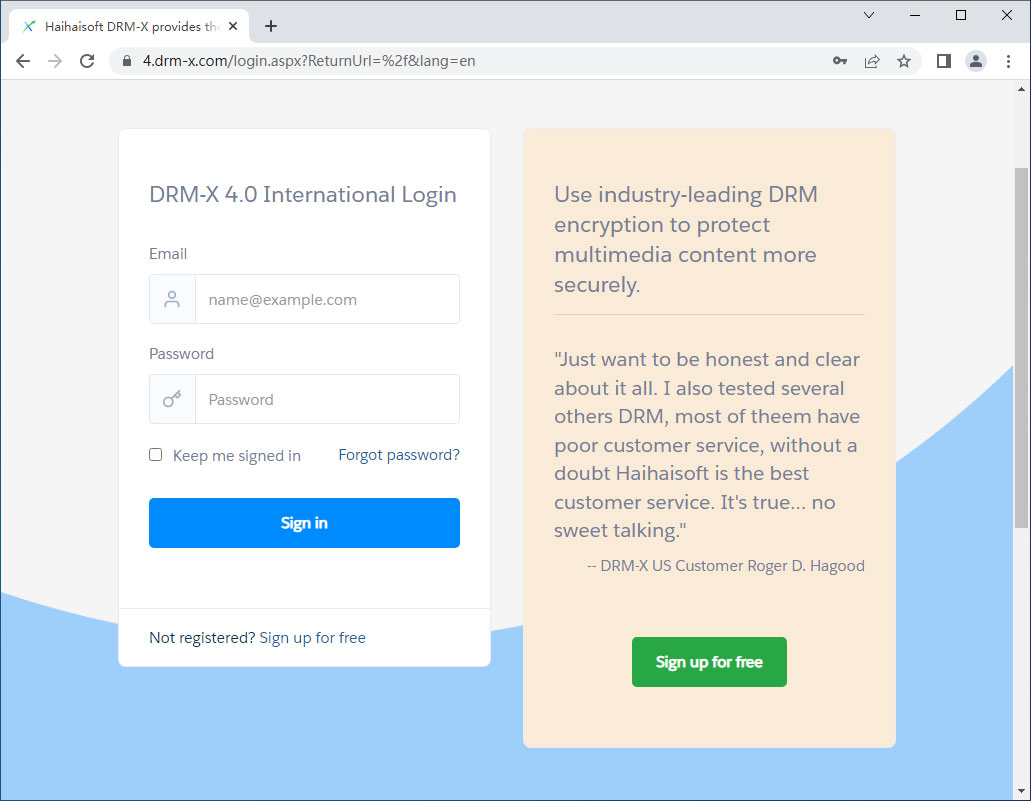
- Features: Uses a dedicated Xvast secure browser to open encrypted PDF files. Supports screenshot prevention and user watermarking (e.g., username, IP address). Offers hardware binding to ensure files are accessible only on authorized devices. Restricts printing and editing, requiring user credentials to obtain a viewing license.
- Advantages: Prevents screenshots, includes user watermark display, and hardware binding for access control.
- Disadvantages: Requires a dedicated browser, which might affect user experience.
- If you need quick encryption and are not concerned about screenshots, SmallPDF Online Encryption is a convenient option.
- If you require industry-standard compatibility and comprehensive functionality, Adobe Acrobat PDF Encryption is a reliable tool.
- If you need high-level security and strict control over file distribution, DRM-X 4.0 PDF Encryption Software is the best choice, especially suitable for protecting sensitive information and critical documents in enterprises.
Selecting the appropriate encryption solution based on actual needs can better safeguard your information security.
2. Protection of Website Management Backend
-
Watermarking User Information
- Incorporate watermarks on the backend to display user login information, aiding accountability during breaches.
-
Dynamic Encryption for Website Content
For company website management backends with high-security requirements, dynamic encryption solutions such as DRM-X 4.0 Dynamic Website DRM Protection, can be utilized. This approach provides:
- Prevent screen recording and screenshot Prevention: Effectively prevents users from capturing website management backend information via screen recording or screenshots.
- Account-Password or Facial Recognition Login with Hardware Binding: Requires employees to log in to the management backend with their account and password and complete authentication. The hardware binding feature ensures that only authorized devices can access the management backend. For example, employees are restricted to logging in from their office computers and cannot log in from other devices.
- Dynamic Watermark Functionality: Adds dynamic watermarks to backend content to further enhance security.
-
Multi-Layered Security Measures
- Implement IP restrictions, ensuring backend access is limited to internal company networks.
- Introduce authentication mechanisms, allocating read-only, editing, or downloading permissions as needed.
3. Training and Supervision
-
Employee Training
- Conduct regular security training to raise awareness and simulate data breach scenarios to improve emergency response.
-
Monitoring and Auditing
- Establish oversight mechanisms to regularly audit internal data usage and backend access, identifying and mitigating potential risks.
- Use monitoring software to track employee activities and backend operations, ensuring compliance.
Mature Solutions for Enterprise Data Security
The industry offers various well-established Digital Rights Management (DRM) solutions to address the aforementioned issues, particularly focusing on enterprise-level data encryption technologies that provide flexible and efficient protection methods.
For instance, DRM-X solutions specialize in comprehensive encryption of corporate documents and dynamic website encryption. Key features include: Prevent screen Recording, Screenshot Prevention, Dynamic Watermark Display, Hardware Binding, restricting document editing and controlling document printing. These functionalities fully meet the security requirements of enterprises.
By leveraging these solutions, businesses can implement strict access controls on internal documents and backend content, enhance overall security, and reduce the risk of data breaches. If you are interested in such technical solutions, you may explore their applications in content encryption and permission management to select the most suitable approach for safeguarding your enterprise's data security.

